The First Step of Windows Post-Mortem Debugging
August 26th, 2009
I’m starting a new series of posts talking about something I’ve learned in past few years with respect to debugging. You can find the sample code used in these articles in Codeplex. (I use Codeplex instead of SourceForge simply because it is much faster for my network. There is no endorsement nor affiliation with Microsoft.)
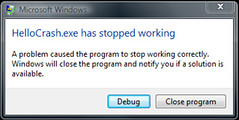
Let’s start with the simplest program, HelloCrash. Compile and run this program introduces a crash.
Most users will click Close here, but that’s ok. We can still find some traces in the Windows Logs, Application:
This actually gives out quite a few important information as highlighted. We can do some work here before jumping into dump collection and analysis. Interestingly, I’ve seen so many people has blind belief of memory dump analysis so that they forgot there are still easy ways of doing things 🙂
In this case, we have the module name and offset, which means we could directly find out the crashing line from map files and assembly outputs. Although these information could be misleading, but it’s worth a try. We know the faulting module is HelloCrash.exe, and offset is 0x1002. The map file said
Preferred load address is 00400000
…Address Publics by Value Rva+Base Lib:Object
0000:00000001 ___safe_se_handler_count 00000001
0000:00000000 ___ImageBase 004000000001:00000000 _wmain 00401000 f HelloCrash.obj
0001:00000017 @__security_check_cookie@4 00401017 f MSVCRT:secchk.obj
…
So it seems that the crash is from _wmain function (offset 0x1000 to 0x1016), and the offset within the function is 0x2. If your project has assembly file generated, it’s almost immediate that you can find the line
; 9 : TCHAR* p = NULL;
00000 33 c0 xor eax, eax
; 10 : _tprintf(_T(“Hello, crash: %s\n”), *p); // deref NULL pointer
00002 0f b7 00 movzx eax, WORD PTR [eax]
This example is so simple that we can see a deref of NULL pointer from assembly output directly, and then we can correct the error.
I’ll discuss some more ways of getting to the crashing point in coming articles. Stay tuned 🙂